
Definitively eliminating unnecessary, unneeded and unwanted data from an enterprise that generates more data exhaust every day is a much harder slog than it seems.
In this series, we’ve discussed how to overcome the operational challenges of data eradication, addressed the capacity issues of eliminating data at scale, and explained how software-based data sanitization procedures offer a safer and more efficient alternative to simple erasure or hardware destruction.
All of these techniques for reducing the risk of unwanted data exposure have been proven in the field. Now we’ve come full circle to discussing how to answer the question: “Are we there yet?”
Shredders will shred, until there’s a reason not to
If a company could eradicate data from media far more cheaply through software-based routines, while recouping equipment costs, and reducing electronic waste, they would automatically move away from shredding drives, right?
One key factor—operational risk—leads enterprises to automatically retain the wasteful practice of shredding drives as a cost of doing business.
A large enterprise may have thousands of failed, obsolescent or unused drives that come up for erasure every week, typically gathered in bins at the company’s datacenters and offices, or collected by technology partners and contractors.
The data generated by an software-driven erasure process can be overwhelming. Volumes of information can come in on the status of each drive’s eradication—perhaps through syslogs, or more likely, through an assurance via email from people who say the job is done.
There will always be a certain percentage of drives that are unresponsive to electronic eradication methods or provide uncertain indicators about the success of a deletion procedure.
As usual, the exceptions and blind spots are where operational risks lie. If a certain percentage of drives cannot be proven to be erased, they are instead slated for destruction, and lost value entails.


Thinking globally and acting programatically
Best-in-class technology companies are already thinking about the hard problems of balancing expediency and risk elimination through shredding, versus the more measured approach of rehabilitating or recycling storage media.
Best-in-class organizations establish a set of KPIs around continuously improving several common factors for their eradication program, including measures such as:
- Total throughput: The total number of media assets running through the deletion process per week or per day.
- Process time: How long each drive takes to run through the eradication process. Reducing this number is critical for operationalizing the process.
- Touch time: Calculating how much manual effort is required on the part of a human engineer or operator to attend to each eradication process, or a group of processes. Reducing this factor reduces labor costs, but ultimately less touch time really means automation is working more efficiently.
- Success rate: The percentage of drives that verifiably complete the erasure process.
- Failure rate: The percentage of drives that cannot be verified as erased. These drives may be set aside and run through the process again.
- Recovery rate: The percentage of drives that are provably erased and eligible for repurposing or refurbishment.
- Recycle rate: The percentage of drives that are erased and sent for recycling. These drives may be obsolete or otherwise damaged and not fit for use, but can contribute to environmental goals.
- Destruction rate: Total number of drives sent for shredding.
- Resale or reuse value: Revenue gained, or costs avoided, due to the ability to resell drives to a third party buyer, or redeploy drives within the org instead of buying new ones.
While this may look like a lot of factors to follow, don’t worry. Most of these criteria aren’t continually monitored, but instead reviewed weekly, or even quarterly, to see if a trend is changing, and understand how the process can be further improved to deliver value over the long term.
If an alert threshold or anomaly does pop up, a program manager can jump in and take a closer look, and determine if an incident or escalation is warranted.
Answering the self-assessment challenge at Revert, Inc.
I really appreciate case studies that demonstrate how a company can ‘eat its own dogfood’ in improving its own processes to meet the needs of customers.
Revert, Inc. is a global services firm that delivers on-site data sanitization and enterprise IT asset disposition services to enterprises, data centers and storage technology companies.
While delivering data eradication services, they found that many of their customers received an initial reduction in process time and success rates through their manual intervention and erasure methodologies, but many customers couldn’t consistently realize reuse and recycling goals for drives without continued manual intervention.
Existing drive erasure solutions weren’t able to provide the level of automation needed for further improvement, so they developed their own data eradication solution that encoded hard-won expertise from the field—Verity ES.
There are still people working on erasure at client sites, as someone still occasionally has to pull and sort drives, but their Verity ES solution can now erase hundreds of disks at a time, providing clear telemetry and logging data back through a visibility dashboard where CISOs and CIOs can get an instant view into the eradication process and track the results against their compliance and reuse goals.

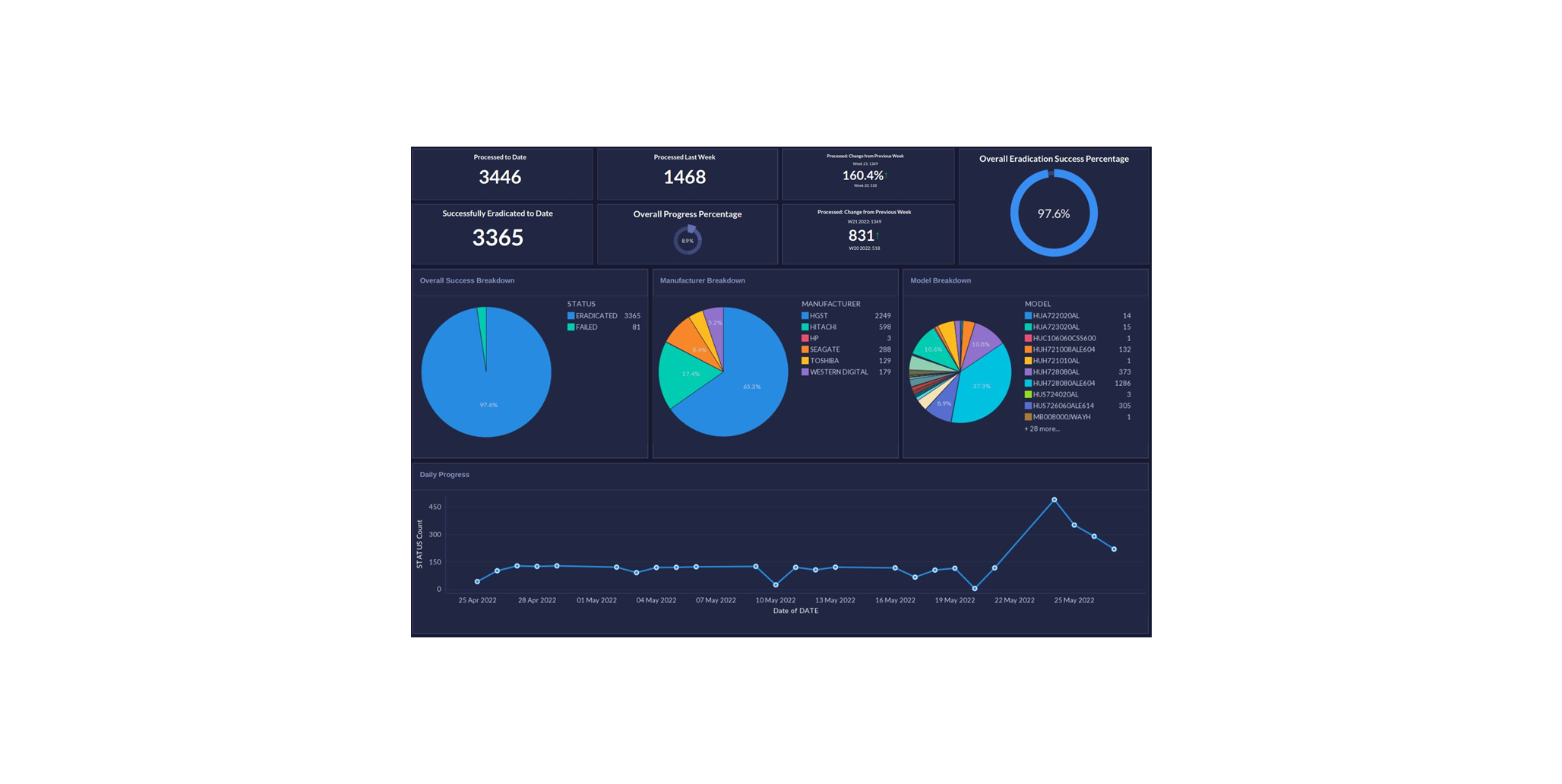
At one of their global leader clients, they were able to improve software-based drive eradication success rates by a full 20 percentage points – from 75% to as much as 95% with . Furthermore, by feeding problem drives back into the system, they were able to identify one particular set of hard drive models that was causing most of the failures, so that particular line could be written off for shredding without the cost or hassle.

The Intellyx Take
Data eradication success isn’t just about erasing disks. It’s about shifting our perception of the role data centers play in protecting valued data, avoiding operational risk, and returning value back to the business.
Executives and customers have a stake in the operational performance of removing unwanted data from the world with new automated erasure processes, and therefore it has become a necessary part of a company’s overall security posture.
The visibility gained can reduce regulatory compliance headaches and security auditing efforts as well.
©2023 Intellyx LLC. Intellyx retains editorial control over this document, and no AI chatbots were used in writing this article. At the time of writing, Verity ES is an Intellyx client. Image source: William Warby, flickr CC2.0 license.


